OpenVPN and Android
To be honest I use OpenVPN quite rarely on my Android tablet, and it happens only when I need to access certain locations that tie me to a certain IP address. This type of connection could be more often used when the tabled would serve as an email reading device at a company that would restrict email usage without a VPN.
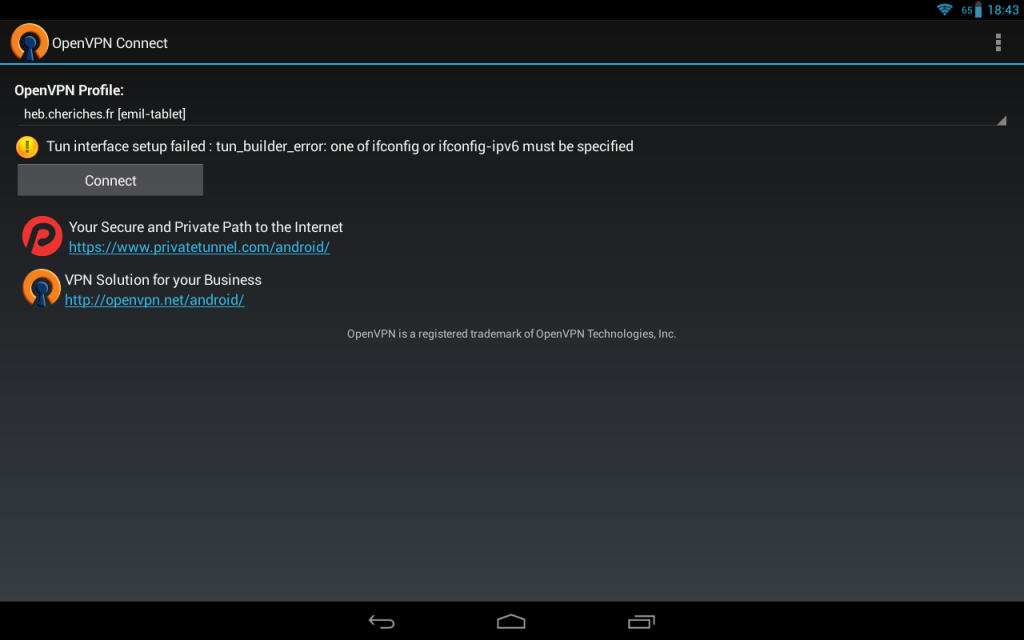
So, today, I open my OpenVPN Connect app and try to connect. And I get this message:
Tun interface setup failed: tun_builder_error: one of ifconfig or ifconfig-ipv6 must be specified
As a good guy the first thing I do is to google the message and what I get are only stupid answers like “brackets inside the config file are wrong”. I take a look in my config file, there are absolutely no brackets. WTF!?
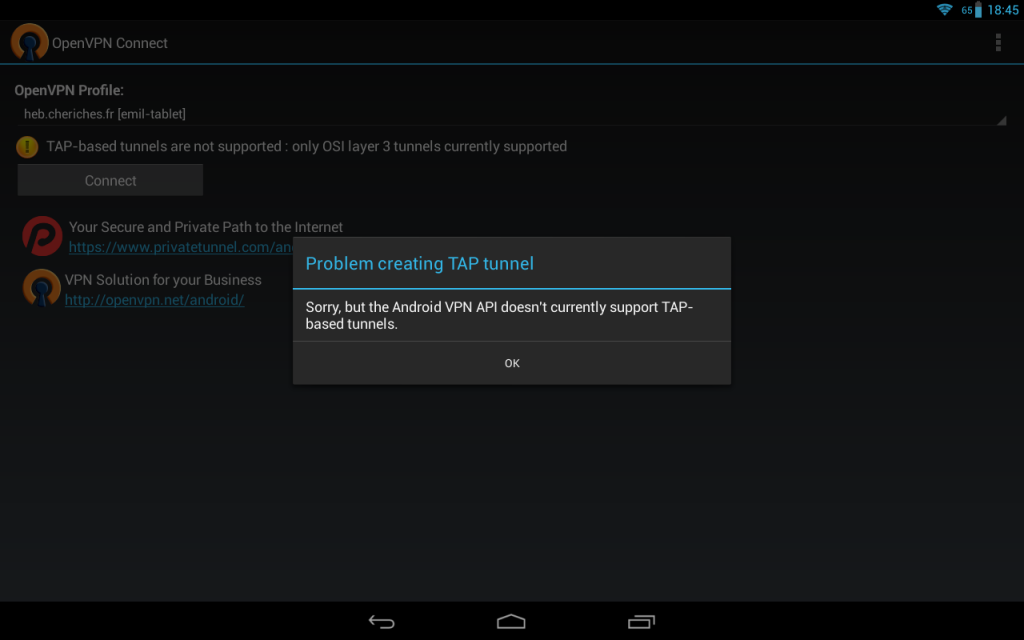
Looking further in the config file I realise that I changed the config on the server, so that it would use a “tap” interface instead of a “tun” one. Ok, I change that in the tablet’s config file and try to connect again. Another error message:
Sorry, but the Android VPN API doesn’t currently allow TAP-based tunnels.
WTF again!
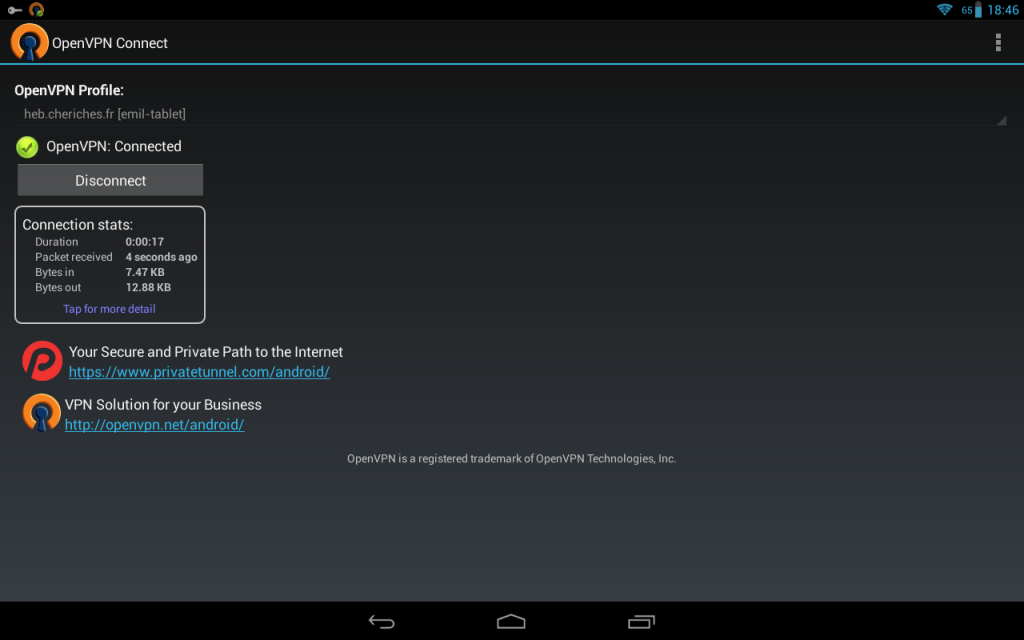
I ended up creating a new config on the server, to make the connection on a different port, using tun-based configuration, and reversed tablet’s configuration to using tun-based interface.
And everything works! Magic!

I’m running into this same issue except my server config isn’t using a tap device. Would you be willing to post your server and client config files?
So, the server is something like:
port YOUR_PORT
proto udp
dev tun0
ca ca.crt
cert server.crt
key server.key
dh dh1024.pem
server 10.11.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push “redirect-gateway def1 bypass-dhcp”
push “dhcp-option DNS 10.11.0.1 8.8.8.8”
client-to-client
keepalive 5 120
persist-key
persist-tun
status openvpn-status.log
verb 3
And the client:
client
dev tun
proto udp
remote YOUR_SERVER YOUR_PORT
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert client.crt
key client.key
ns-cert-type server
verb 3
Thanks, that did it! Changed a few of my settings to match yours and this connection oddity disappeared.
Thank you, i think solved mine too.